Introduction
A more neutral description of NIS 2 is given
There is almost a religious believe in NIS 2 as an impotent cybersecurity directive. This believe is fueled by consultant companies making good money providing guidance in the deployment of NIS 2.
Machine-to-machine (M2M) communication
Especially in a critical IT structure machine-to-machine (M2M) communication is used in a communications network, without any human intervention. This is the case when many Internet of things (IoT) devices are involved. In such special communication rules apply. Anything issued by one system needs to be fully understood by the recipient system, meaning that every bit put on the communication channel must be accounted for in a detailed specification. If the two communicating systems are developed by different vendors, that specification must be an international standard.
Figure 1 – Machine-to-machine communication
This is illustrated in figure 1 above.
Communication phases
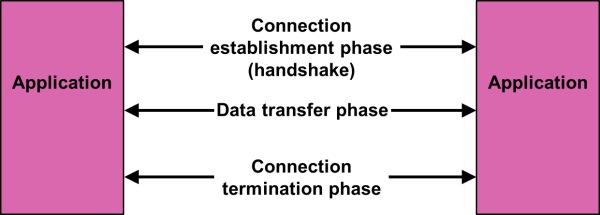
Figure 2 – Communication phases
The figure above illustrates the separate phases of communication between two systems:
- The connection establishment phase, also called the handshake, is a phase where the rules for the connection are established.
- The data transfer phase, where data is exchanged.
- The connection termination phase.
The handshake

Figure 3 – Information exchange during the connection establishment phase
During the connection establishment phase multiple types of information are exchanged:
- To ensure the identities, the two systems must exchange digital signatures based on a robust digital signature cryptographic algorithm. Use of password is not feasible in this environment. Exchange of digital signature also requires exchange of public-key certificates. In addition to ensure identity (authentication), digital signatures provide integrity as the verification of a digital signature will fail if the data in an exchange is modified during transmission.
- If encryption is to be used, the exchange will establish what symmetric-key algorithm to be used for encryption.
- Under the data transfer integrity may instead of digital signatures be ensured by integrity check values, also known as message authentication codes. There are symmetric key algorithms that allow encryption and integrity to be performed as a single operation.
- During the handshake symmetric key can be generated based on key establishment methods, i.e. specific cryptographic algorithms. Symmetric keys are used both for encryption and integrity check values.
Data transfer phase
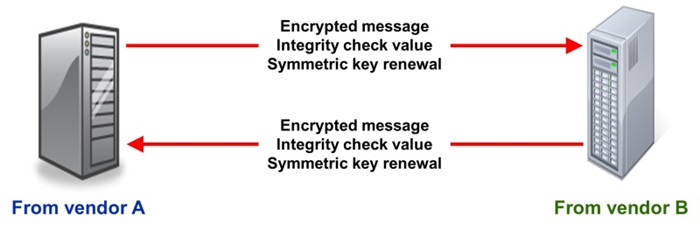
Figure 4 – Information exchange during the data transfer phase
During the data transfer phase communication is protected making use of the cryptographic algorithms introduces during the association establishment phase.
- If confidentiality is required, the messages exchanged may be encrypted using the symmetric keys and the symmetric key algorithms established during the handshake.
- Integrity code values are an alternative to digital signatures during data transfer and for authentication. It can only be used digital signature is used to get secure authentication during handshake and it has been ensured that both entities in a communication have the same set of symmetric keys.
- The symmetric keys must be renewed at time intervals to avoid much information is encrypted by the same key.
Application-to-application communication
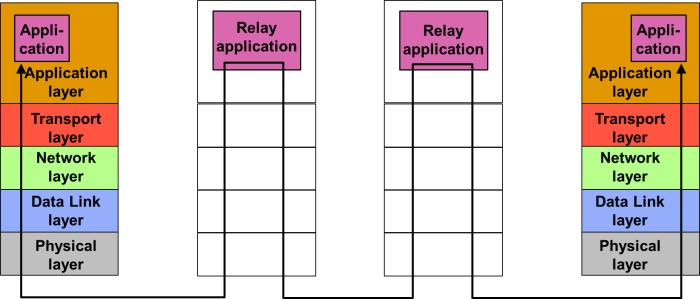
Figure 5 – Association between applications
In the previous, connection between two system was considered, However, the communication is between some entities within the two systems and in many cases, it is between applications (also called application entities) within the two systems, e.g., having a client server relationship. This illustrated in figure 5.
Figure 5 also illustrates the layered communication model. The original opens systems interworking (OSI) is a seven-layer model. In the Internet a model, the top three top layers are collapsed into a single application layer. This model is relevant for most communication systems.
A connection between two application entities is called an (application) association. An association may be seen as some kind of agreement achieved over a transport connection.
Figure 5 also illustrates that zero or more intermediate systems may be act as transparent relays for an association. Encryption, digital signatures, etc. are end-to-end functions without any interference by the relay systems.

Figure 6 – Simplified view of association between applications
For simplicity, the model in figure 6 is used. The model illustrated i figure 5 is then implied.

Figure 7 – Connection on the transport layer
A much-used cybersecurity method is transport layer security (TLS). As the name imply, it operates at the transport layer and has all the capabilities discussed above. TLS is used by browsers to establish cybersecurity.
OpenSSL is a popular open source implementation of TLS.
Network considerations
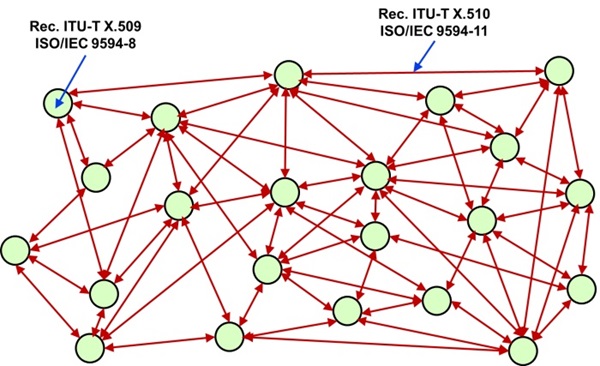
Figure 8 – Network example
Figure 8 shows a network of many entities that are fully interconnected. at the application layer by associations. In real life that may not be realistic, but in any case, there may be many connections in a network. The number of entities may be much larger than shown in the figure, especially in a network with many IoT devices. There are examples of several hundred IoT devices in network.
A connection should of security reasons have set symmetric key that different from symmetric keys used by any other association meaning that many different symmetric keys need to be generated and renewed.
There are two ways of establishing symmetric keys:
- By key distribution where a key distribution centre distributes keys to the systems. It is a little tricky to get the necessary cybersecurity and the technique is not scalable.
- On every connection or association, the symmetric keys are established by exchanges between the two partners in a communication using so-called key establishment methods (KEMs).
