Erik Andersen’s activities
This site is concerned with cybersecurity activities as a small contribution to make Denmark and Europe a safer place.
(Will be under continuous development)
Standard
bodies

The Standards Development Organizations (SDOs) primarily mentioned here are ITU-T, ISO and IEC.
IETF and NIST are other SDOs that make contributions to cybersecurity standardization.
Beyond NIS2 and firewalls

NIS2 may be a threat to cybersecurity, as
it is falsely believed that NIS2 is sufficient for cybersikkerhed.
Be active in standardization

Cybersecurity standardization is a multiple headed beast covering procedural aspects, security requirements on network components and detailed specifications for how to satisfy requirements.
ASN.1
as a tool

Abstract Syntax Notation One (ASN.1) is the perfect tool for creating communication standards. It flexible, easy to read and it supports multiple encodings (multiple binary encodings, XML encoding and Jason encoding).
ITU-T X.509

ITU-T X.509 is the framework for public-key infrastructure (PKI). It is one of the most important cybersecurity standards supported secure banking, e-government, etc. since 1988. New requirements are queuing up.
ITU-T X.510
While ITU-T X.509 provides support for entities, ITU-T X.510 provides protection for communication protocols for connections between entities. It also specifies how to migrate cryptographic algorithm.
ITU-T X.508

ITU-T X.508 complements ITU-T X.509 and ITU-T X.510 by giving a comprehensive description of cryptographic algorithms, the mathematics behind and best practise on establishing a PKI.
ITU-T X.DPKI
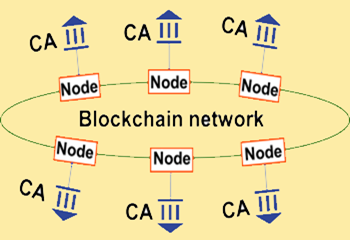
DPKI stands for decentralized PKI and is a PKI where PKI domains are interconnect using blockchain technology and where PKI information is stored in the ledger making it available worldwide.
EU activity
EU Rolling Plan

EU in its rolling plan for 2025 has identified cybersecurity / network and information security to be a foundational driver for ensuring the Internet. This include NIS 2 and EU Cybersecurity Act
NIS 2

EU has issued a new cybersecurity directive Network and Information Security 2 (NIS 2). This directive is an enhancement to the existing NIS directive directed against organizations.
EU CSA

EU Cybersecurity Act (CSA)
EU CRA

From 2027 the EU Cyber Resilience Act (CRA) requires manufactures and retailers to ensure cybersecurity of digital components throughout the lifecycle of their products
ENIGMA

During the second World War Germany used a system called Enigma for encryption and decryption of data. The encrypted data was transmitted as Morse code to be intercepted by anyone.
Crypto agility
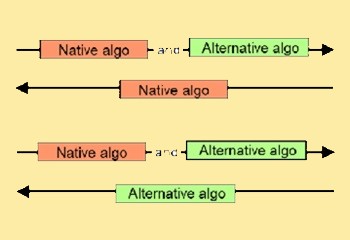
Cryto agility is important in the light od quantum computers. Crypto agility is the ability to adapt to more secure cryptographic algorithms without significant changes to system structure.
